Subsequently, there is a growing need for IDSes to detect new conduct and proactively establish novel threats and their evasion strategies.
An Intrusion Detection Method (IDS) adds more security for your cybersecurity setup, rendering it very important. It works along with your other protection tools to catch threats that get previous your key defenses. So, In case your major process misses something, the IDS will alert you on the menace.
The look of some products could be referred to as acquiring "form more than operate". That is certainly, the shape of the item is aesthetically pleasing but won't actually do its occupation quite very well. Share Make improvements to this answer Adhere to
An intrusion detection procedure (IDS) is a device or computer software software that screens a community or devices for destructive exercise or coverage violations.[one] Any intrusion exercise or violation is often possibly documented to an administrator or gathered centrally employing a safety details and event administration (SIEM) technique.
What exactly is MAC Deal with? To communicate or transfer information from 1 computer to another, we want an handle. In Laptop or computer networks, many types of addresses are released; Each individual will work at a unique layer.
An IPS is similar to an intrusion detection technique but differs in that an IPS may be configured to dam possible threats. Like intrusion detection units, IPSes are employed to observe, log and report routines, Nonetheless they may also be configured to halt Sophisticated threats with no involvement of the technique administrator. An IDS typically basically warns of suspicious exercise happening but won't stop it.
Coordinated assault: A community scan menace allocates a lot of hosts or ports to distinctive attackers, rendering it complicated for your IDS to figure out what is occurring.
is almost always a vowel, how can I explain to when It is just a consonant? Wondering back, I don't Feel my education and learning at any time included the distinction between them, we just memorized which letters were which.
It tells gadgets which percentage of the handle belongs on the network and which identifies person equipment. By undertaking this it helps to select which gadgets belong to the exact same nearby netwo
If you'd like a proverb, it may be "Not all that glitters is gold", Though what on earth is not great is just not essentially poor.
Wikipedia has a cryptic remark that “British English particularly will make use in the slash instead of the hyphen in forming abbreviations.” Hyphen?
Intrusion detection methods are comparable to intrusion prevention units, but you will discover dissimilarities worthy of understanding about.
What is pharming? website Pharming is really a scamming practice in which destructive code is put in over a Personal computer or server, misdirecting consumers to fraudulent Web sites... See full definition What's pink teaming? Purple teaming would be the apply of rigorously difficult designs, procedures, techniques and assumptions with the adversarial method.
From time to time an IDS with a lot more advanced capabilities will likely be built-in by using a firewall so as to have the ability to intercept refined attacks coming into the network.
 Nancy Kerrigan Then & Now!
Nancy Kerrigan Then & Now!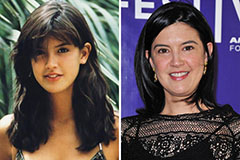 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Lisa Whelchel Then & Now!
Lisa Whelchel Then & Now! Brooke Shields Then & Now!
Brooke Shields Then & Now! Katey Sagal Then & Now!
Katey Sagal Then & Now!